Multi-Factor Authentication (MFA) has now become a ubiquitous requirement for online services. Whether they seek to qualify for cyber-insurance coverage or seek approval from the Federal Trade Commission (FTC), the requirements to apply multi-factor authentication are similar.
But there are a lot of misconceptions about what creates an effective MFA strategy. A recent study of 500 financial organizations worldwide found that there is broad confidence in the security departments’ approach to authentication, with 90% saying that their approach is mostly or completely secure. Yet, this faith is dangerously misplaced given that 80% of organizations were breached in the last 12 months due to believed authentication vulnerabilities. It is surprising to see the seeming disconnect between perceived and actual authentication security. Especially with the recent high-profile attacks stemming from authentication weaknesses, such as the Colonial Pipeline ransomware attack that forced the shutdown of the largest pipeline in the U.S., the $34 million stolen this year from the cryptocurrency exchange Crypto.com after hackers found a way to bypass their MFA controls or the recent extensive Uber breach by an 18-year-old.
On the customer-facing services that organizations provide to the end-users (e.g. online banking), the survey found insecure practices to be even more prevalent, with only 43% of financial institutions using traditional MFA methods for customer authentication. On top of that, a staggering 38% of FIs are allowing the use of social identity credentials (Google, Facebook, Linkedin IDs) which means the authentication is trusted to these third parties. Most mind-boggling is that 28% are requiring only a username and password which is widely understood to be the weakest, most phishing-susceptible authentication method.Finally, almost half (47%) believe that phishing-resistant multi-factor authentication already is key to their authentication strategy and another 51% believe it plays a part. There is obvious confusion here, highlighting a need for better education and training around how MFA should be implemented to be truly effective.
Bypassing MFA
To understand where most common MFA methods fall short, let’s review common attack vectors to bypass them.
Passwords, PINs, and Knowledge-Based Questions
These knowledge-based authentication factors are not even considered multi-factor authentication. They are the most basic means of authentication based on something the user knows or remembers. The means to gain access to knowledge-based credentials are numerous ranging from phishing sites, simply asking them over the phone, looking at victims’ Facebook accounts to learn about their “Favorite X”, or buying troves of compromised credentials on the dark web and performing credential stuffing which is based on the premise that people re-use their passwords across multiple services which makes it easier for attackers to gain access to multiple accounts of a single victim. Password reuse was in fact the key vector for the initial Colonial Pipeline breach.
SMS text messages and one-time passcodes (OTPs)
SMS is still the most ubiquitous means of second-factor authentication because it leverages a person’s phone number and requires the user to have only very basic technology proficiency.
A user’s SMS text messages can be accessed by attackers in a variety of ways. The first is via SIM swaps, which occur when a victim’s phone number is ported to another SIM card that the attacker has in his phone. This is a very “visible” attack as the victim loses cellular service. A more subtle approach uses SMS communication business services as was demonstrated by a hacker to a Vice reporter to receive all of his SMS messages without any indication on his part.
Apart from these more sophisticated approaches, codes that are sent over SMS are viewed by the user, and just like a password, can be phished or social-engineered from a person by an attacker operating in a separate channel (for example, pretending they are calling from a call center to help reset an account.).
Device Identification
Device Identification (Device ID) is a passive authentication method that binds users to specific devices and relies on device security measures (PIN, pattern, password, biometric) to assume only the device holder can access the accounts from it.
This approach has a few shortcomings, some related to key assumptions behind it and some to its technological implementation.
The assumption that only the device owner can access a device is flawed. Many people share their device access pin/password/pattern with their spouse or with their kids. Some even add the biometrics (fingerprint) of these family members to their devices. Device security measures can be also compromised by malware on the device stealing or disabling these credentials.
The other shortcomings stem from how these solutions are implemented. In some cases, the device identification is done by simple measures such as a web browser cookie. A cookie is essentially a file that can be copied from device to device, and thus if it is transferred to the attacker’s device, it will be identified as the trusted victim’s device. Another method looks at various device characteristics like browser type, screen size, or CPU type. These aspects are ineffective when looking at mobile devices and tablets as they all share the exact same characteristics, and thus make the Device ID the same for all devices of the same make-model. Even when used on a laptop, the frequent updates and changes in browsers lead to only about 60% accuracy in correctly recognizing device ownership.
Device Biometrics
In the last couple of years, a strong push toward passwordless authentication has been made throughout the industry. Most passwordless authentication solutions rely on using device biometrics (FaceID, Fingerprint) to verify the user and release a cryptographic key that in turn authenticates them into the app or service based on Fast ID Online (FIDO) protocols.
The FIDO passwordless approach has great benefits from a few aspects. For one, there are no passwords involved which eliminate phishing risk and password reuse issues. Second, there is an inherent two-factor authentication that includes verifying the user via the device biometrics and authenticating the device to the service using a cryptographic key exchange. Third, it is quicker than typing a password, receiving a pin over SMS and typing it, and less error-prone to human typing errors.
The recent Apple, Google, and Microsoft announced that they will support PassKey authentication based on this approach and are expected to increase its adoption across industries.
With all that said, the FIDO approach has two gaps that undermine the level of trust organizations can assume from this authentication method:
* Biometrically verifying the user – or is it? browsers and apps which allow the user to use the device biometrics, also allow the user to fall back to alternative authentication to the device/app. The alternative in most cases is a password or PIN code which brings us back to the shortcomings of these authentication measures discussed above. If anyone knows your device password/pin/pattern they can release the FIDO cryptographic key and access the online service on your behalf.
* The initial enrollment of a device passwordless FIDO authentication to a service is done without verifying the affiliation between the device owner identity and the service account owner identity. That means that if an attacker gets access to my bank password, they can access it with their device and link them to the biometric on their own device. There is no process to ensure the credentials are being used by the account owner when generating the cryptographic key for future access.
Together, these shortcomings make the device biometric a great convenience measure, but a limited addition in terms of actually protecting online accounts.
Getting MFA Right
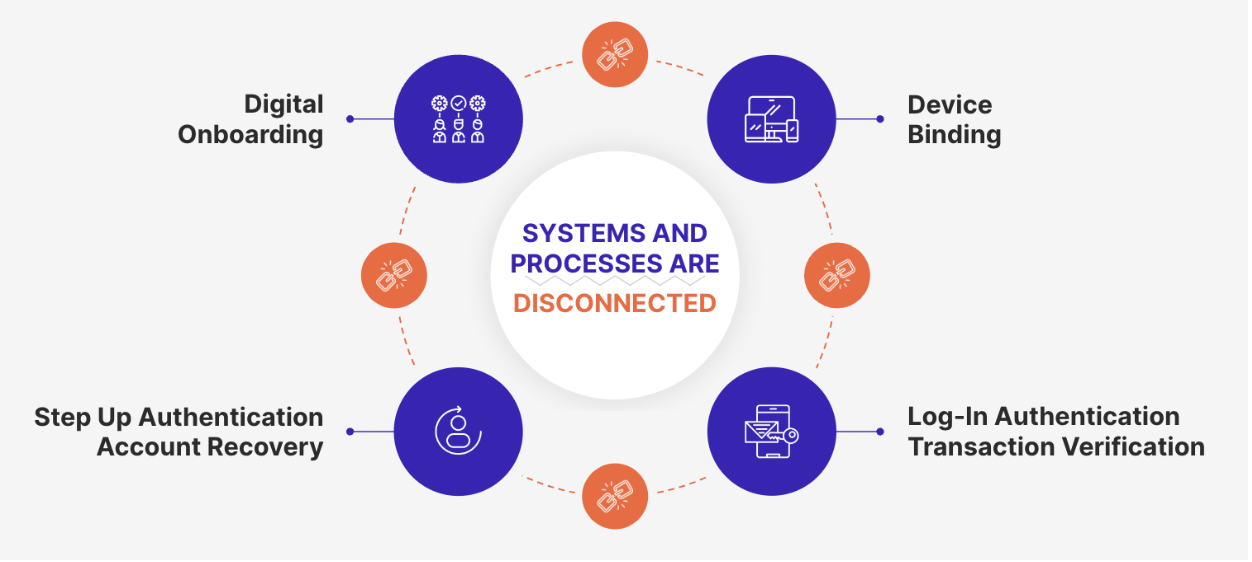
Establishing correct implementation of MFA requires taking a broader look at how trust in a users’ identity is established and maintained. Today organizations employ a stack of solutions to perform onboarding, authentication, recovery, and orchestration of a users’ journey.
Digital onboarding generally involves analysis of various signals including device longevity, known IP addresses, past anomalous behavior and/or verification of a holder’s identification credentials and selfie comparison.
Once the identity has been verified, a user will typically be invited to create login credentials (user name and password) which are used to access and utilize online service.
This is the root of the failure of traditional MFA. Any implementation that separates the selfie biometrics collected in onboarding from downstream authentication will ultimately be exploited by attackers.
Getting MFA right requires the biometric data from onboarding to be connected to downstream authentication and utilizing a second factor as a pointer or binder. For example, if the selfie collected at onboarding is associated with a phone number or device, it will be very hard for an attacker to pass both factors.
There are some challenges with implementing this holistic approach however, that should not be discounted:
* Seamless solutions that achieve this have not been readily available, leaving enterprises to stitch together different elements of the tech stack which is complicated
* Deploying and managing biometrics raises privacy and data management issues
With new technological breakthroughs and well thought out system design, these challenges are being overcome. For example, Anonybit’s MFA solution leverages multi-party computing and zero knowledge proofs to preserve biometrics privacy while connecting the different elements of an existing tech stack in a seamless manner. Selfies from the digital onboarding process are ingested into the Anonybit system, sharded for storage and kept in a decentralized manner for downstream authentication. Used at login, to verify transactions, enable self-service account recovery and other step up authentication actions, the platform’s APIs communicate with different orchestration platforms. Device, phone number, email address and other factors are linked to the user’s biometrics for secure MFA and compliance.
Click here to learn more about Anonybit’s biometric MFA solution.